Configure column-level security
Column-level security provides admins with the flexibility to restrict or grant access to column-level data. This granular control over data access allows your organization to secure sensitive or confidential information, ensuring it’s accessible to authorized users only.
This document explains how to use user attributes to enforce column-level security in a dataset.
User requirements
- To configure user attributes, you must be assigned the Admin account type.
- To reference existing user attributes in a dataset, you must be granted Can edit dataset permission.
Understanding column-level security
Column-level security is managed through team assignments, user attributes, and dataset configurations. When you utilize user attributes for column-level security, you can dynamically set column accessibility based on attribute values set for specific teams. You can also use column-level security to grant access to individual columns within a table for different embed clients.
Benefits of column-level security:
- Data privacy: Secure columns that contain sensitive information, including personal identifiers (e.g., social security numbers), financial data, or medical records.
- Data sharing and collaboration: Enable controlled data sharing and collaboration. Organizations can share select columns with external parties or partners without exposing the entire dataset.
- Data confidentiality in multi-tenant environments: In multi-tenant systems or cloud-based environments where multiple clients or orgs share the same infrastructure, column-level security ensures that each tenant's data remains isolated and protected from other tenants.
- Data masking and anonymization: Combine with data masking and anonymization techniques to protect sensitive data while still allowing certain authorized users to work with pseudo or obfuscated values.
Configure column-level security
-
In the Administration portal, create a user attribute or open an existing one to edit.
When you create the user attribute for column-level security, ensure you define a default value. If you don't specify the default value, Sigma automatically assigns attribute value "2" as the default, which restricts column data for applicable users.
-
Assign attribute values to teams using the following preexisting assigned values intended for column-level security:
Assigned value Column-level security outcome 0 Column data is included in workbooks by default 1 Column data is available, but not added to workbooks by default 2 Column data is unavailable (restricted) in workbooks -
Open the applicable dataset or create a new one, then grant team permissions (for more information, see Share datasets). The assigned permission type doesn't affect the results of column-level security.
To prevent unintentional results or errors, avoid using user attributes in a materialized dataset.
-
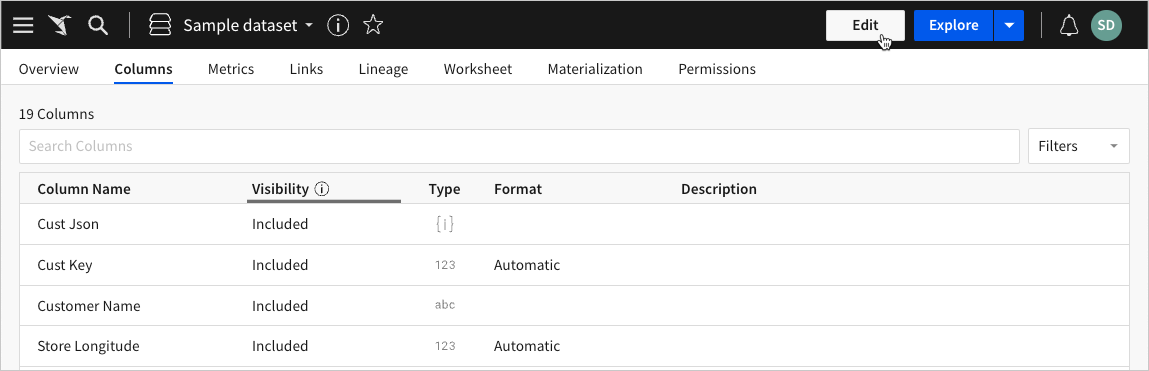
Select the Columns tab, then click Edit in the dataset header.
-
Locate the column you want to configure for column-level security, then click the Visibility dropdown and select the applicable user attribute.
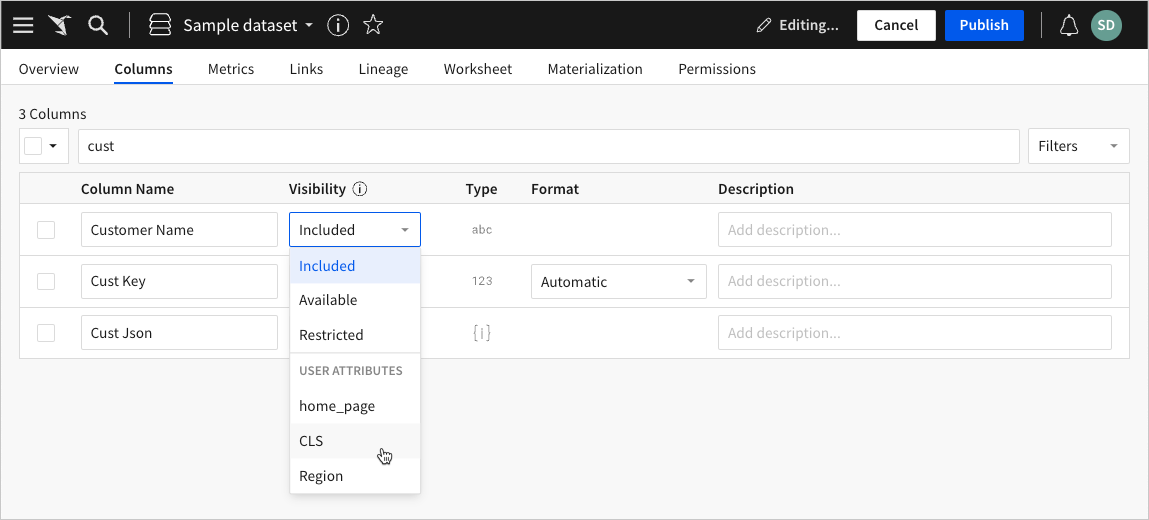
-
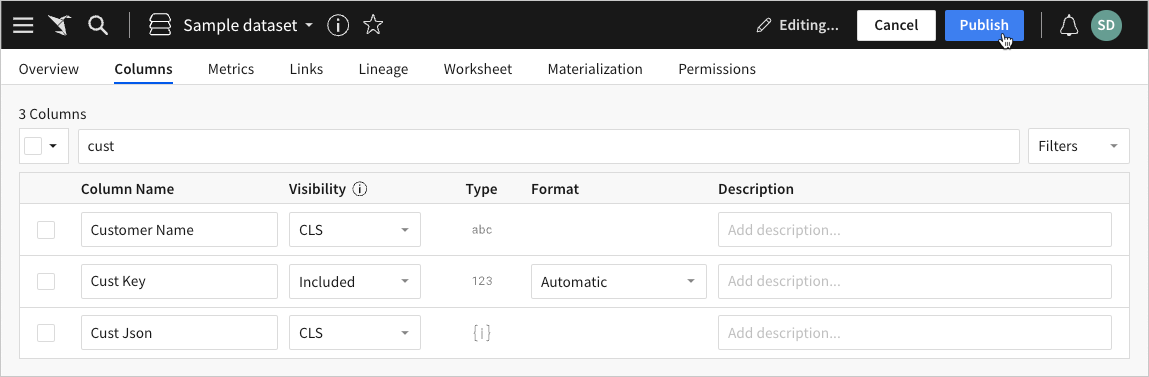
Repeat step 5 for all columns that require column-level security, then click Publish in the dataset header to save your edits.
-
You can now create a workbook that leverages the dataset with column-level security. When you share the workbook with applicable teams, the data is included or restricted based on each user's team assignments, user attributes, and corresponding dataset visibility configurations.
Example configuration
This example demonstrates an implementation of column-level security.
A Sigma organization has two teams: Team A and Team B. Members of Team A require access to the Domain column in an existing Customer dataset, while members of Team B need to be restricted from viewing that same data.
To begin configuring the required data security, an admin first creates a Domain CLS user attribute. They assign the attribute value "0" to Team A (to include data) and the attribute value "2" to Team B (to restrict data).
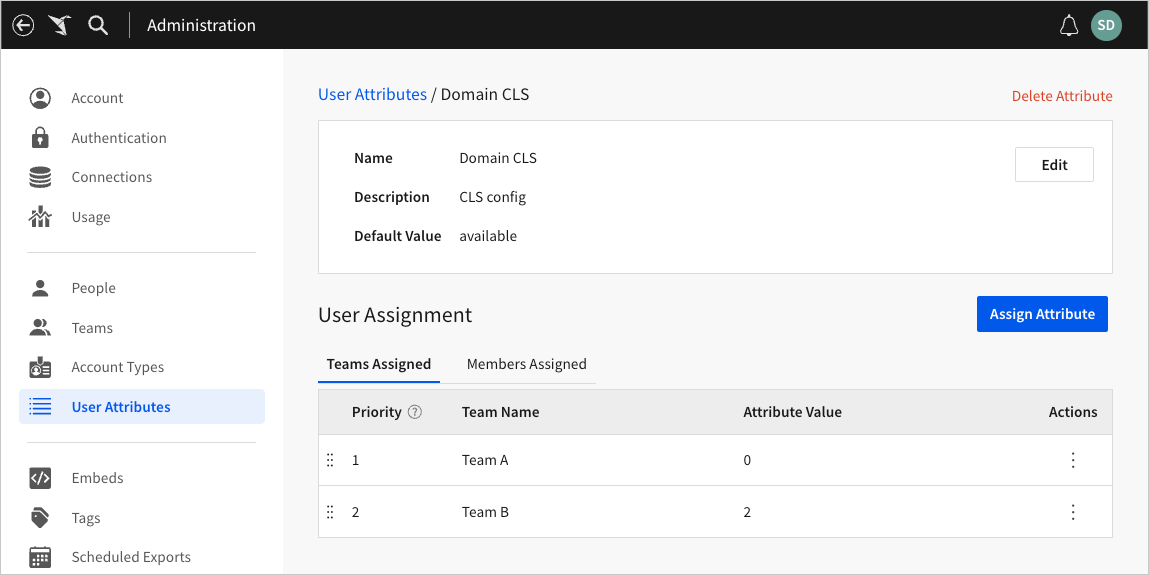
The admin opens the Customer dataset and selects the Permissions tab to verify that Team A and Team B are both granted permission to access the dataset. They then select the Columns tab and click Edit in the dataset header to enable column edits.
In the Columns tab, the admin finds the Domain column, then clicks the corresponding Visibility dropdown field and selects the Domain CLS user attribute. This applies the Domain CLS attribute values assigned to Team A and Team B.
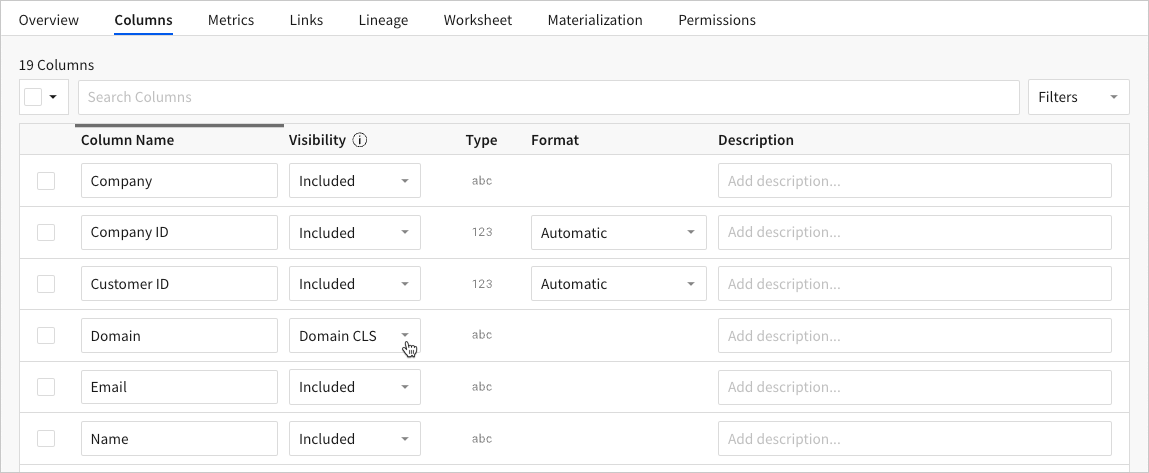
After the admin saves the dataset edits, they create a workbook from the dataset (which adds a table with all the dataset columns) and share it with the teams.
-
When a members of Team A opens the workbook, Sigma displays all data in the Domain column.
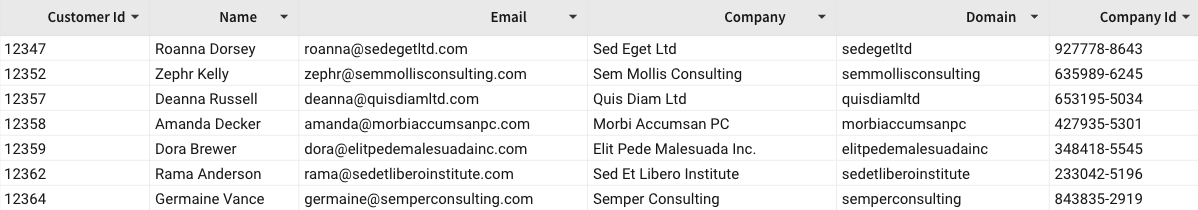
-
When a member of Team B opens the workbook, Sigma obfuscates the data in the Domain column and displays "invalid query" in each row because the data is restricted for that user.
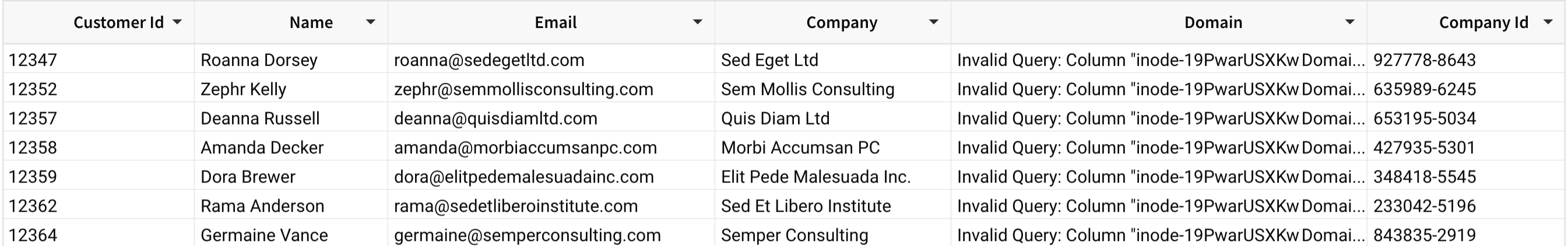
Updated about 2 months ago
